Security Profiles |
Security Profiles are used to define multiple levels of system access permissions within specified companies. Administrators can Create New Security Profiles, Copy Security Profiles, Modify Security Profiles and generate a Report of Security Profiles. Also see Related Tasks.
Navigate To: System>Administration>Create a New Profile
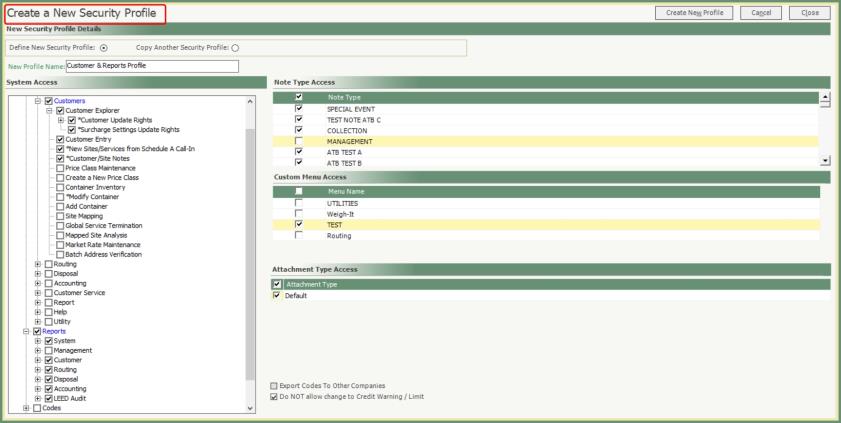
- Enter a New Profile Name.
- Select each System Access that applies to this Profile.
- To select access to all click All.
- Click the + to expand the tree to each menu group.
- Click the - to collapse the menu group.
- An asterisk (*) indicates an additional function within a program.
- Example: Add a New Site or New Service from Schedule Call In.
- Example: Update Credit Warning or Limit from Account Inquiry.
- Remove the check mark to deny access.
- Menu Groups with one or more systems with denied access will display in Blue.
- Select applicable Note Type, Custom Menu and Attachment Type Access.
- Select applicable customer Menu Access.
- If the security profile will be using the Export Codes to Other Companies, place a check in the box.
- If the security profile will be denied access to change Credit Warning or Limits, place a check in the box.
- Click Create New Profile.
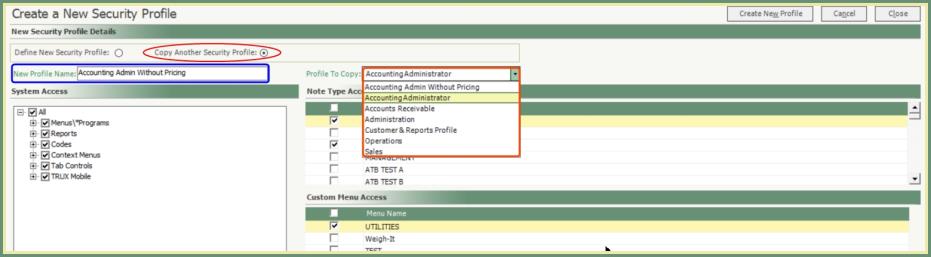
- Select Copy Another Security Profile.
- Enter the New Profile Name.
- Select the Profile To Copy from the drop down.
- Click Create New Profile.
Navigate To: System>Administration>Manage Security Profiles
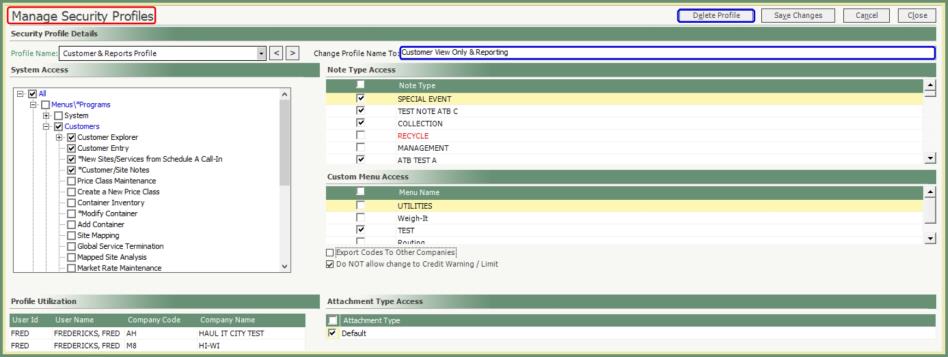
- Select a Profile Name from the drop down.
- Make Changes. Optional Changes:
- Add or Remove System Access.
- Change Profile Name.
- Delete Profile.
- Add or Remove Note, Custom or Attachment Access.
- Add or Remove Export Codes or Credit Warning/Limit Changes.
- Profile Utilization will include all Users/Company with this Profile.
Navigate To: Reports>Report Center>system>Security Profile Listing
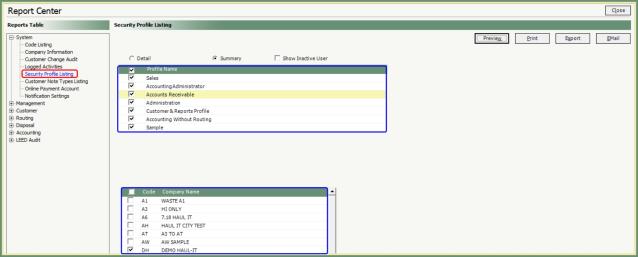
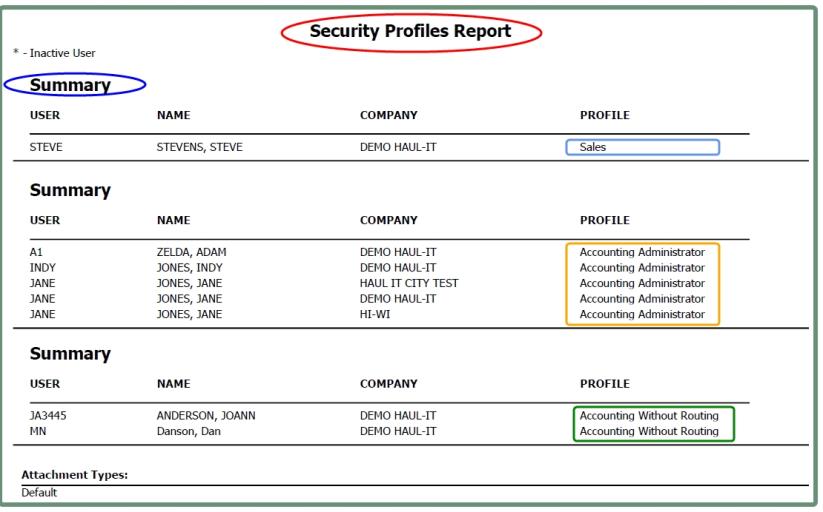
- Select Detail or Summary.
- Detail: Lists each granted System Access Menu for each Profile Name selected.
- Summary: Lists only the granted Security Profile name by user/company.
- Select Show Inactive User if you would like inactive users included on the report.
- Select all or specified Profile Names to include.
- Select all or specified Companies to include.
Report Sample: